Data Storage Transmission and Cloud Services Policy
Policy Number: IT-08
Effective: 05/01/2020
Last Revised: 09/22/2023
Responsible Executive: Executive Vice President & CFOO
Contact Information: 765-677-2605
I. Scope
This policy applies to all employees, student workers, contractors, third-party vendors, and anyone who accesses or handles data on behalf of Indiana Wesleyan University (IWU). It encompasses data in all formats, including electronic, physical, and covers data stored on-premises, in the cloud, or transmitted through various communication channels. The Data Classification Policy details how IWU data is categorized.
II. Policy Statement
At IWU, we recognize the critical importance of safeguarding university and constituent information and maintaining the highest standards of data security. Our aim is to ensure the confidentiality, integrity, and availability of IWU PROTECTED or IWU SENSITIVE data while adhering to all relevant information security frameworks, legal and regulatory requirements.
III. Reason for the Policy
Federal/State laws and information security frameworks place a premium on an organization’s ability to understand the risks of IT services and systems and to make the appropriate determinations about risk tolerance. This document addresses information security and data privacy concerning the use of cloud and on-premises computing services utilized by in scope personnel and the storage of data within these service areas.
IV. Procedures
A. The Data Storage matrix below references the IWU data classification tiers, as defined in the IWU Data Classification Policy, and outlines the acceptable storage of IWU data.
![]()
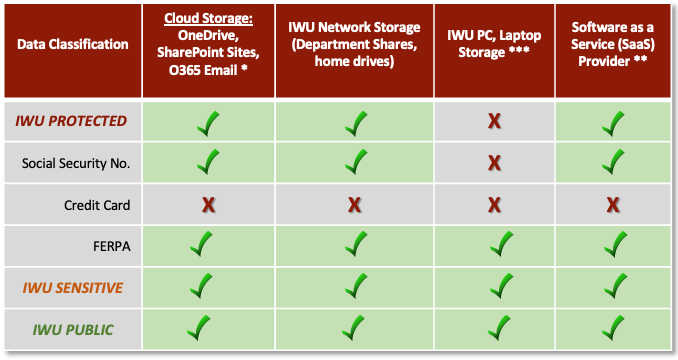
Note: Within the IWU PROTECTED data tier are exceptions and clarifications.
1. * Cloud Storage: IWU PROTECTED, IWU SENSITIVE, and IWU PUBLIC data are permitted to be stored on the University’s approved cloud storage platform: Microsoft’s Office365 for Business. If an employee or department is employing a third-party cloud file storage vendor, they must declare this activity to the IT Project Management Office (PMO). A path to mitigate data exposure risk or to migrate the data from a non-approved vendor to a university approved cloud storage service may be necessary and must be planned out accordingly.
2. ** SaaS (Software-as-a-Service) Storage: Historically, IWU has entered into contracts with cloud application providers to better serve the university and its constituents. As part of an IT, Information Security Office (ISO) and Enterprise Architect review process, the requesting IWU department must include the PMO in the initial planning meetings with the vendor when discussing all IWU-hosted data and system integrations. No contract is permitted to proceed until the process referenced in the SaaS, Cloud Hosting, Software and Hardware Procurement Policy has been completed.
3. *** Removable Device Storage: It is strongly recommended that IWU personnel utilize IWU owned mobile devices (laptops, tablets) to edit any tier of university data. These devices should already be protected with IWU related security controls. The use of external devices like USB drives is not approved unless reviewed and permitted by the Information Security Office (ISO).
4. Data Encryption: All IWU PROTECTED and IWU SENSITIVE data must be encrypted at rest using industry-standard encryption algorithms. Data that cannot be encrypted at rest for technical reasons must be reviewed by the Information Security Office (ISO) to determine risk.
5. Data Retention and Destruction: Data should be retained only for as long as necessary to fulfill business or legal requirements. Once data reaches the end of its retention period, it must be securely deleted or disposed of using appropriate methods to prevent unauthorized retrieval. More information on data retention requirements can be found in the IWU Document Retention and Destruction Policy.
B. The Data Transmission matrix below outlines the IWU data classification tiers and the proper encryption and transmission requirements and restrictions when utilizing University approved email, fax, or chat applications.
![]()
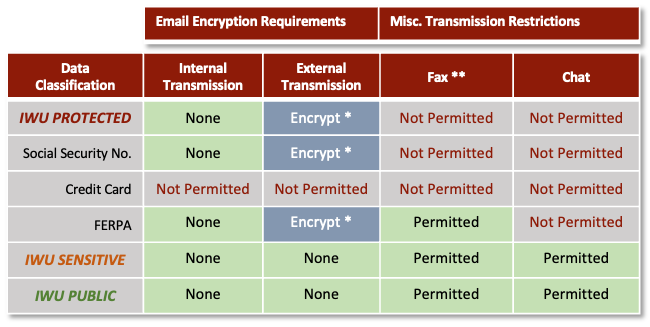
Within the IWU PROTECTED DATA tier are exceptions and clarifications as noted.
1. In scope personnel should prioritize the utilization of these services (email, chat applications) to transmit data as opposed to a means to store data.
2. For security and university standardization purposes, utilizing University approved storage services and systems is required as noted in the SaaS, Cloud Hosting, Software and Hardware Procurement policy.
3. * Secure Communications: Data transmitted over networks must use secure communication protocols, such as TLS/SSL, to prevent eavesdropping and unauthorized interception. Data transmitted via email can further be encrypted via the IWU Secure transmission procedure found in the university KB.
4. ** Fax Communications: The sending and receiving, via fax, of IWU PROTECTED DATA, outside of FERPA, is not permitted except as follows:
a. If the employee is using a university approved and PCI compliant e-fax service that encrypts the fax traffic.
b. If utilizing an e-fax solution, information designated as ‘Not Permitted’ may not be stored within the University email system but rather be imported into the University approved document imaging system. The exception to this is credit card information. This MAY NOT be stored either in electronic or hard copy format.
c. If utilizing a traditional analog fax device: The device must be located in a secured area that only the intended recipients can access. The recipients must retrieve the fax, record the information, and dispose of the paper copy as soon as possible utilizing a shredder bin provided by the University and its contracted vendor.
V. Definitions
Software-as-a-Service (SaaS) - A cloud-based software delivery model that allows end users to access software applications over the internet. With a SaaS model, the software is hosted on remote servers, maintained, and updated by the service provider, and made available to customers via web browsers, mobile apps and APIs.
Example SaaS solutions utilized by IWU:
- Microsoft email and file storage
- Salesforce
- Slate
- Parchment
VI. Related Information
A. Data Classification Policy - This policy outlines the criteria that determines what data classification type a given piece of data should be classified under for examples of each category of IWU data. Reference this policy for specific examples of each category of data.
B. Document Retention and Destruction Policy - This policy provides for the systematic review, retention and destruction of documents received or created by Indiana Wesleyan University in connection with the transaction of institutional business.
C. Not Permitted - File Sharing Cloud Services that are not permitted to be used to store any IWU data except as approved via the SaaS review policy (link):
1. Dropbox
2. Box
3. Google Docs
4. OneCloud
5. iCloud
D. Permissible File Sharing Cloud Service - For file sharing and storage purposes, Microsoft OneDrive for Business has been provided to all faculty, administration and staff. E. IWU Secure Transmission Procedure - This procedure provides message encryption between the sender and recipient and can be received by any email user or system.
F. Compliance with Legal and Regulatory Requirements
1. The University has many federal and international laws that it must follow, these include the Family Educational Rights and Privacy Act of 1974 (FERPA), the Health Insurance Portability and Accountability Act (HIPAA), General Data Protection Regulation (GDPR) and the Gramm-Leach-Bliley Act (GLBA).
2. A relationship with a cloud-computing vendor may also be impacted by private industry regulations. For example, departments at the University that accept credit cards also must follow the Payment Card Industry (PCI) Data Security Standard (DSS) issued by the major credit card companies.
3. Cloud-computing services that use, store, or process University data must also follow applicable University policies. Such policies may include Information Technology Services policies and the University's data handling requirements.
G. SaaS, Cloud Hosting, Software and Hardware Procurement Policy - This policy outlines the requirements for acquiring and implementing new software and hardware assets at Indiana Wesleyan University as well as any cloud-based software or hosting solutions.